2 minutes
Process Doppelgänging - code injection technique
What is Process Doppelgänging?
Process Doppelgänging is a code injection technique which allows to load and execute arbitrary code in the context of a benign process without calling Windows API functions commonly invoked to achieve code injection. The technique was published by Tal Liberman and Eugene Kogan at Black Hat Europe 2017. The concept is to abuse NTFS transactions to create a process from a malicious section that is seemingly backed by a benign file. From an attacker’s point of view this is desirable as antivirus software may fail to scan the code of the malicious section and analyze the content of the benign file instead.
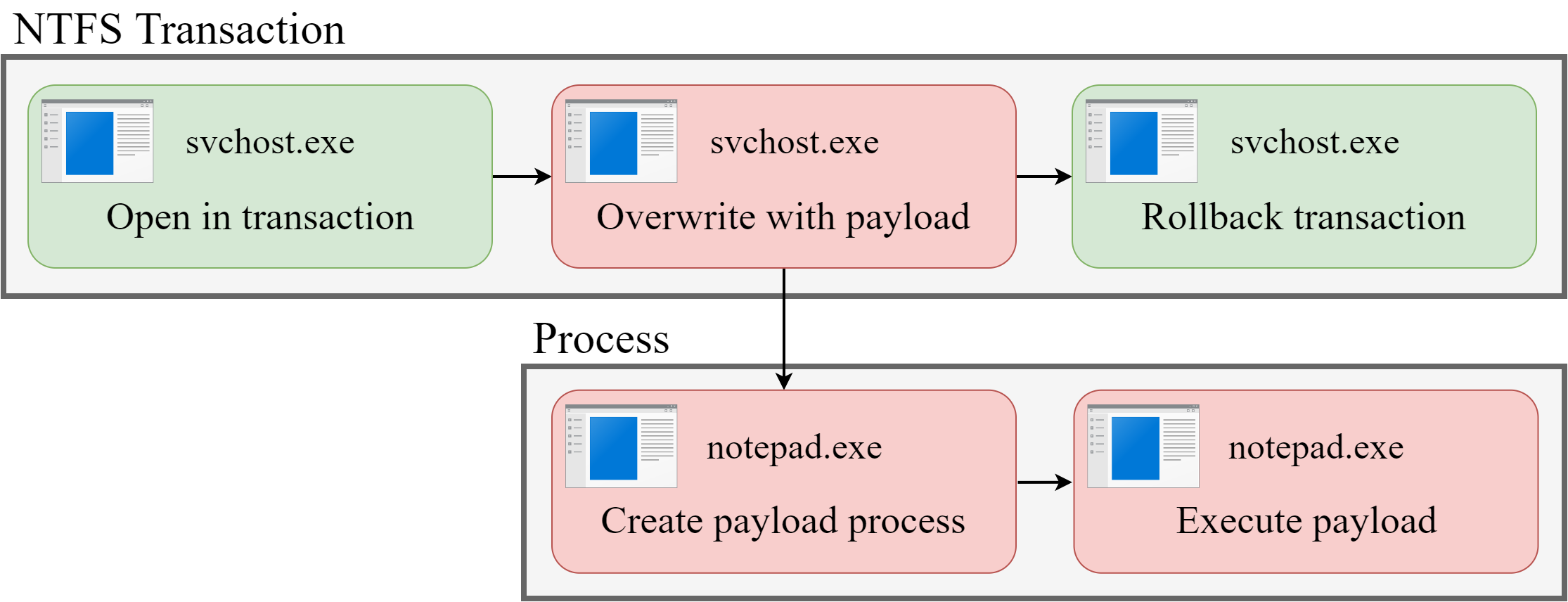
The image above illustrates the concept of Process Doppelgänging by creating a malicious notepad process from an overwritten svchost executable. The first step is opening a benign binary file such as svchost.exe in a transaction. In the next step, the file is overwritten by the malicious payload which is then mapped into memory. Subsequently, the transaction is rolled back which restores the changes on the file system. The section mapped into memory is not affected by this rollback. This results in a payload section in memory that is linked to a benign file such as svchost.exe. Then, a process based on the payload section is created by calling the low level Windows API function NtCreateProcessEx. Finally, the attacker creates the first thread of the process to start execution at the start address of the payload.
This technique is still prevalent on Windows 7 at the time of writing, but has been patched on Windows 10 where a Windows Defender driver blocks process creation from files with pending transactions. Since this method requires direct calls to low level Windows API functions, support for WOW64 must be implemented manually. We could not find an implementation providing WOW64 support. According to malware analyst hasherezade, implementing WOW64 support is feasible but tedious, since it requires manually filling in many parameters that otherwise are handled by the Windows loader.
In 2018 security researchers at Kaspersky Lab identified that the SynAck ransomware employed this technique. Later, security researchers from enSilo uncovered that more than 20 malware families had already employed this technique in 2018. They discovered a loader they named TxHollower to bring Process Doppelgänging to malware families such as FormBook, LokiBot and SmokeLoader. We suspect that malware performs Process Doppelgänging when it invokes the NTFS transaction API since transactions are rarely created. We dump the process when NtCreateThreadEx is called to start execution.
Prototype implementation
My Process Doppelgänging implementation is available on my GitHub.